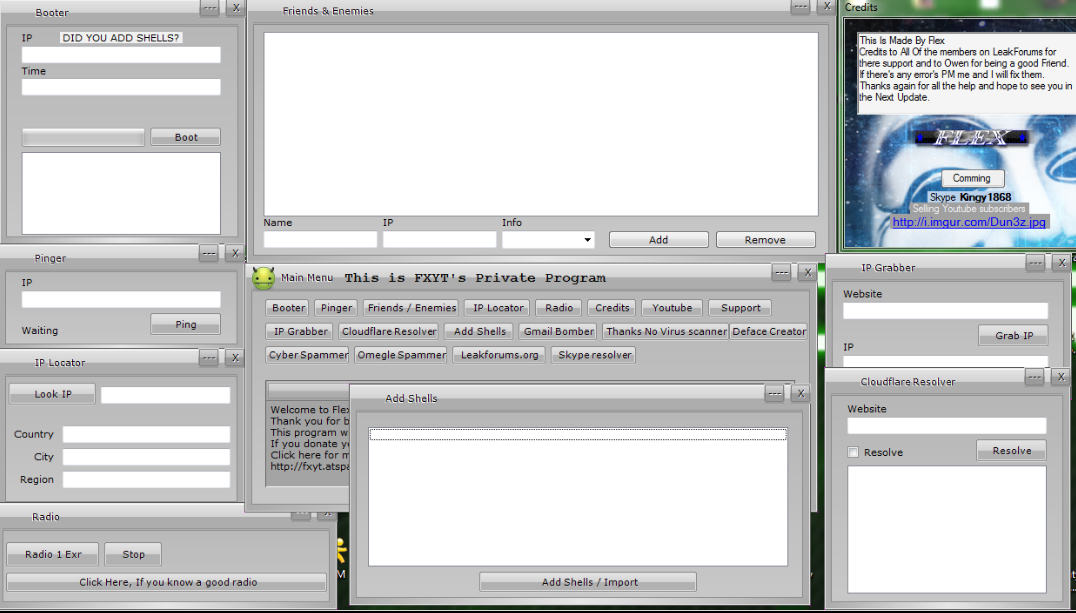
A mi también me molesta un poco, sobre todo cuando usan imágenes de servidores literalmente lento, demora mucho la carga,
Quizas podrían hacer algo con el success del ajax, para que cargue de igual de manera aunque no cargue todo, aunque perdería su función
Pero ojo, no todo lo bonito es funcional.
Saludos!
Quizas podrían hacer algo con el success del ajax, para que cargue de igual de manera aunque no cargue todo, aunque perdería su función
Pero ojo, no todo lo bonito es funcional.
Saludos!